
RFC 6749 OAuth 2.0 defines an authorization framework which enables resource authorization without exposing sensitive user credentials such as passwords.
The OAuth2 framework defines several client types (public and confidential) as well as flows (implicit, authorization code, and several others). For typical Qt applications the client type should be considered as public native application. The public implies that the application isn't trusted to hold secrets, such as passwords, embedded within the shipped binary.
RFC 8252 OAuth 2.0 for Native Apps further defines the best practices for such applications. Among other things, it defines the Authorization Code Flow as the recommended flow. QtNetworkAuth provides a concrete implementation for this flow, and it is also the focus of this documentation.
QtNetworkAuth provides both concrete and abstract OAuth2 classes. The abstract classes are intended for implementing custom flows, while the concrete classes provide a concrete implementation.
To implement an OAuth2 flow with QtNetworkAuth, two classes are needed:
The authorization code flow is the recommended OAuth2 flow for native applications like Qt applications.
The following code snippet provides an example setup:
QOAuth2AuthorizationCodeFlow m_oauth; QOAuthUriSchemeReplyHandler m_handler; m_oauth.setAuthorizationUrl(QUrl("https://some.authorization.service/v3/authorize"_L1)); m_oauth.setAccessTokenUrl(QUrl("https://some.authorization.service/v3/access_token"_L1)); m_oauth.setClientIdentifier("a_client_id"_L1); m_oauth.setScope("read"_L1); connect(&m_oauth, &QAbstractOAuth::authorizeWithBrowser, this, &QDesktopServices::openUrl); connect(&m_oauth, &QAbstractOAuth::granted, this, [this]() { // Here we use QNetworkRequestFactory to store the access token m_api.setBearerToken(m_oauth.token().toLatin1()); m_handler.close(); }); m_handler.setRedirectUrl(QUrl{"com.my.app:/oauth2redirect"_L1}); m_oauth.setReplyHandler(&m_handler); // Initiate the authorization if (m_handler.listen()) { m_oauth.grant(); }
The Authorization Code Flow has two main stages: resource authorization (including any necessary user authentication) followed up by an access token request. These are optionally followed by access token usage and access token refreshing. The following figure illustrates these stages:
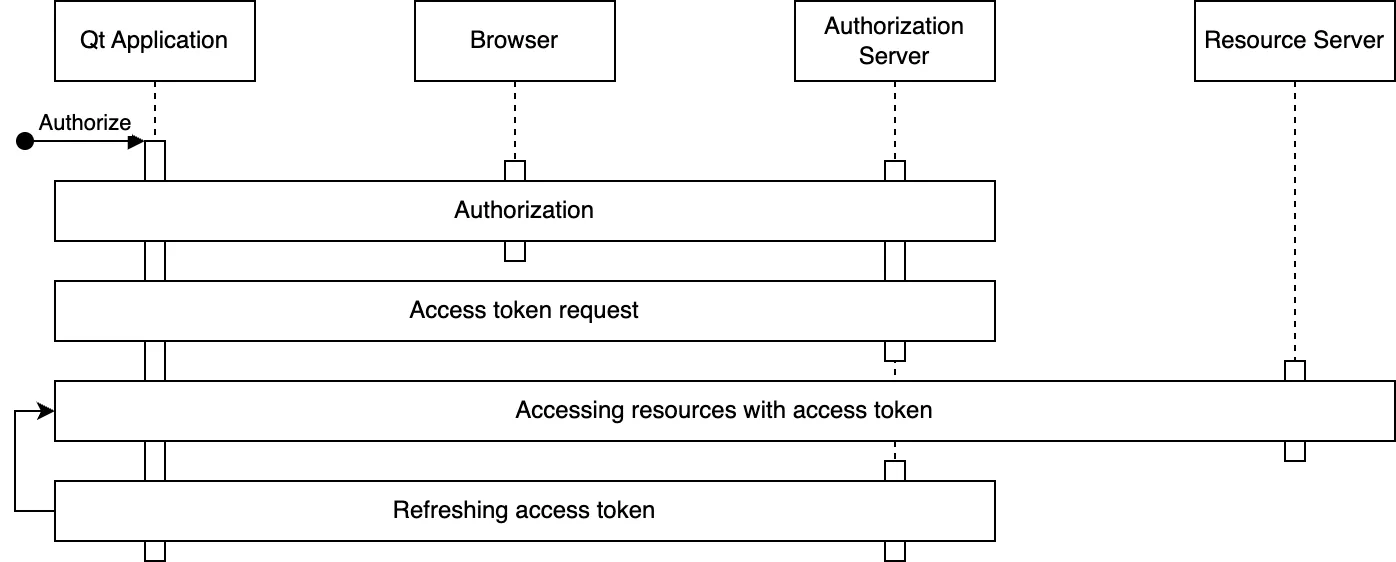
Authorization header is arguably the most common.
OAuth2 flows are dynamic and following the details can be tricky at first. The figure below illustrates the main details of a successful authorization code flow.
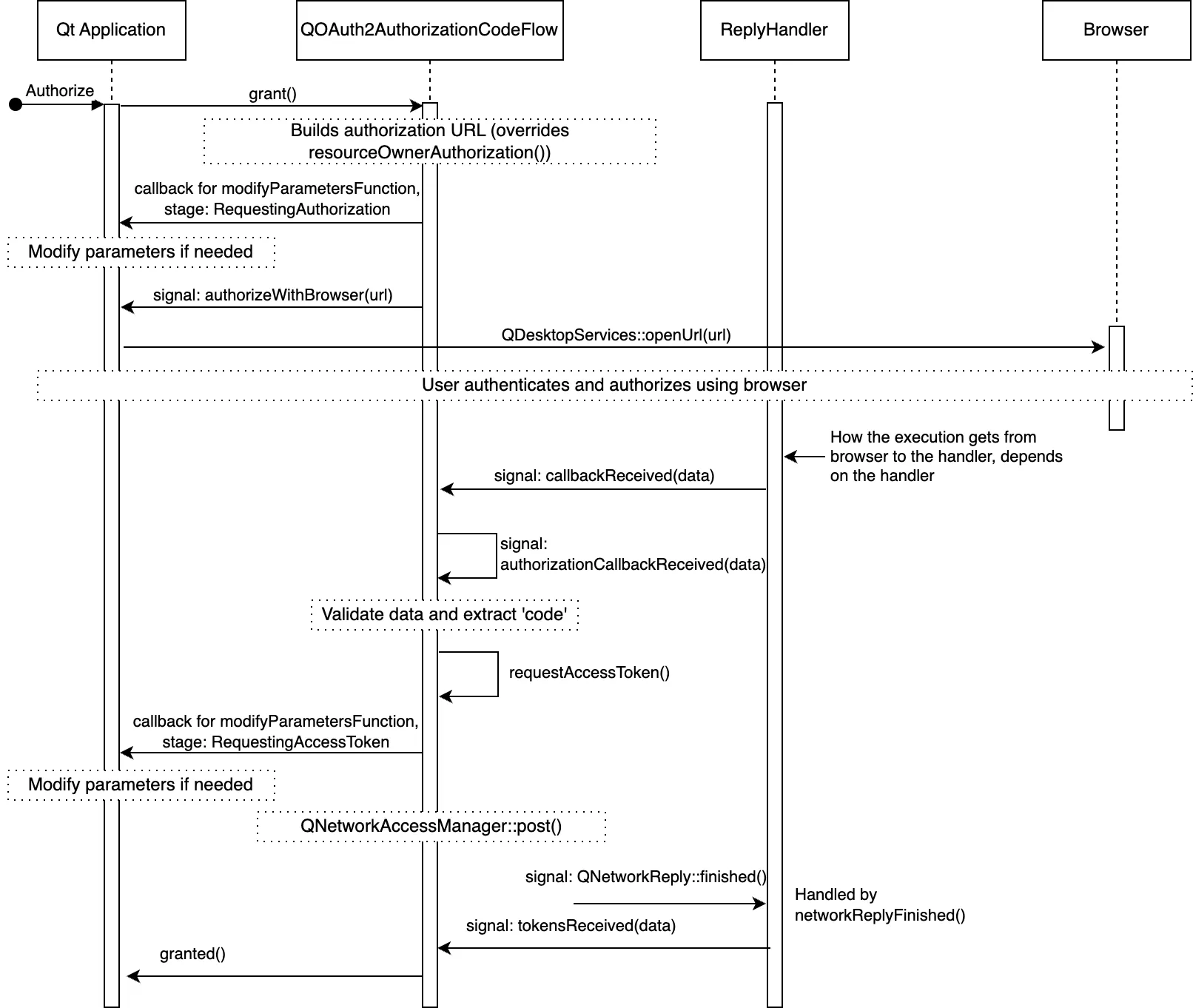
For clarity the figure omits some less used signals, but altogether illustrates the details and main customization points. The customization points are the various signals/slots the application can catch (and call), as well as the callback which is settable with QAbstractOAuth::setModifyParametersFunction().
The decision on which reply hander to use, or to implement, is dependent on the redirect_uri used. The redirect_uri is
where the browser is redirected upon concluding the authorization stage.
In the context of native applications, RFC 8252 outlines three main types of URI schemes: loopback, https, and private-use.
The choice depends on several factors such as:
RFC 8252 recommends using the
httpsscheme for security and usability advantages over the other methods.